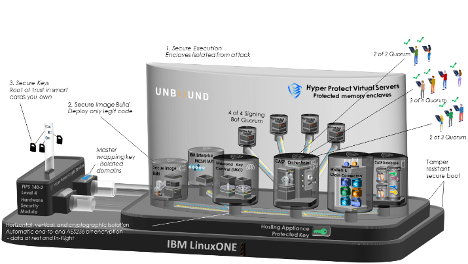
The global pandemic and ensuing economic disruption have accelerated plans for nearly every organization to digitize their business and operations. Our clients are increasing their investments in AI and cloud while moving swiftly to reduce costs and address security with approaches like confidential computing and resiliency.
IBM’s hybrid cloud approach coupled with Red Hat is at the epicenter of this swift and massive transformation. Red Hat OpenShift, the industry’s leading enterprise Kubernetes platform, gives organizations the flexibility to choose where to deploy workloads. It also balances the need to keep workloads close to the data on premises or in a private cloud, while also taking advantage of the agility and flexibility of a public cloud such as IBM Cloud.
Across IBM IT infrastructure, we’re seeing three key use cases for hybrid cloud adoption:
◉ Modernization and containerization of applications to increase developer velocity and provide consistent hybrid cloud management;
◉ Establishing low-latency integration between applications and business-critical data by co-locating cloud-native and traditional applications; and
◉ Making cloud-native apps secure, scalable and resilient with co-optimized software and hardware infrastructure that deliver encryption everywhere and vertical scalability.
As part of this effort, this week we announced new and upcoming hybrid offerings for IBM Z, Power Systems and Storage that give our clients even more flexibility to choose where best to deploy applications in the hybrid cloud, including:
☉ Red Hat OpenShift Container Platform: enables new cloud-native applications to be developed and existing applications to be modernized, with the speed and flexibility to respond to change in a multicloud world. These applications can take advantage of the enterprise qualities of IBM Z, IBM LinuxONE and IBM Power, such as increased performance through co-location with core data. And the choice of enterprise-class data services for hybrid cloud is available with IBM Storage and Red Hat OpenShift Container Storage.
☉ IBM Cloud Pak for Applications: Red Hat and IBM runtimes that help modernize existing applications and develop new cloud-native apps faster for IBM Z and Power Systems.
☉ IBM Cloud Pak for Data: enables organizations to infuse AI throughout their business with a fully integrated data and AI platform that modernizes how data is collected, organized and analyzed already available on IBM Power Systems, planned for November on IBM Z.
☉ IBM Cloud Pak for Integration: helps clients to power digital transformation by efficiently connecting applications and data on IBM Z.
☉ IBM Cloud Pak for Multicloud Management: provides consistent visibility, automation and governance across the hybrid multicloud for IBM Z and Power Systems.
In addition, earlier this week, we announced new Red Hat OpenShift capabilities and support for IBM Storage. Some of the enhancements include the IBM Storage Suite for IBM Cloud Paks expanded support for container-native data access on OpenShift and CoreOS with IBM Spectrum Scale. Furthermore, IBM Cloud Object Storage adds support for the Open Source s3fs file-to-object storage interface bundled with Red Hat OpenShift.For more than twenty years, IBM has worked closely with Red Hat to bring application portability to our clients at every major technology reinvention from Java to Linux; driven by our shared values to provide a flexible, open, hybrid and secured enterprise platform for mission-critical workloads. Together, we are focused on delivering hybrid cloud innovation and differentiation to clients globally.
By working with Red Hat to maximize the value of Red Hat OpenShift on our platforms, we are redefining how organizations create and deliver value, work, compete and transact—all supported by the strengths of the IBM IT infrastructure portfolio: industry expertise in mission-critical business processes; proven security, compliance and governance; the ability to build and run anywhere with consistency; helping clients to automate, predict and modernize workflows and leverage the world’s innovations from confidential computing, to the bleeding edge of security innovation and more. These are all key attributes that will be critical to succeed in the era of hybrid cloud.
This is an exciting next step in our journey to leverage our unique capabilities and help our clients realize the potential of a hybrid cloud business model for their most critical work.
Source: ibm.com