Security analysts are all too familiar with the challenges of alert fatigue, swivel chair type of analysis, and “ghost chasing” spurred by false positives. Facing massive volumes of data coming from an expanding digital footprint and attack surfaces across hybrid multi-cloud environments, they must quickly discern real threats from all the noise without getting derailed by stale intelligence.
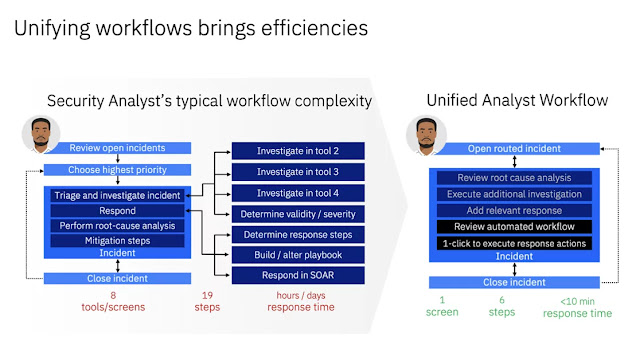
Many organizations have to juggle dozens of security tools, which creates scattered, contextless information that often weakens the foundational triad of cybersecurity: tools, processes and people. To help manage these inefficiencies that can delay crucial threat responses, security operations teams need to explore how to embrace AI and automation.
A day in the SOC
A SOC analyst’s day often includes dealing with limited visibility due to expanding attack surfaces and responding to contextless alerts, which are challenging to decipher. As a result, they frequently spend up to one-third of their day investigating false positives.1 This not only impacts their productivity but also hinders their ability to address about half of the daily alerts, which might be indicators of an actual attack.
The biggest challenges faced by SOC analysts today include:
- Poor visibility: Per The State of Attack Management 2022 report, attack surfaces increased attack surfaces for two out of three organizations in 2022.
- Alert fatigue and disconnected tools: According the same attack surface management report, 80% of organizations use 10 or more tools (e.g. EDR, EPP, NDRs, SIEM, threat intelligence, web traffic, email filtering, system, network and application logs, cloud logs, IAM tools, etc.).
- Keeping up with cyberattacks: IBM’s Cost of a Data Breach report found that 51% of organizations struggle to detect and respond to advanced threats.
- Outdated tools and manual methods: The same data breach report also shows that 32% of organizations lack security automation and orchestration.
- Lack of standardization to fight organized cybercrime globally: The X-Force Threat Intelligence Index reveals signs of increased collaboration between cybercriminal groups.
Adding to these major challenges are other usual suspects such as, increasing complexity, limited resources with increasing cost, and talent shortage (a.k.a skills gap).
As first responders, how SOC analysts prioritize, triage and investigate alerts and signs of suspicious activity defines the fate of attacks and the impact on the organization. When SOC analysts get slowed down by these challenges, it creates a growing defense deficit and breach window, which can expose organization to higher risks.
Finding the needle
Threats hide in complexity and noise and thrive with the inability to keep up with the acceleration of attacks. Attacks can occur in minutes or seconds, while analysts, consumed by manual tasks operate in hours or days. This disparity in speed is a real risk in itself.
Without comprehensive visibility, intelligent risk prioritization, effective detection, proactive threat hunting, and skills building, SOC analysts cannot improve their workflows and evolve with the threat landscape, perpetuating a vicious cycle.
Increasing the security analyst’s productivity is fundamental to scaling cybersecurity in a rapidly evolving threat landscape. After hearing customers and security professionals talk about their core challenges, this efficiency became the goal and IBM designed a purpose-built solution to deliver what is the required to unlock analysts’ productivity.
Investigating and responding fast
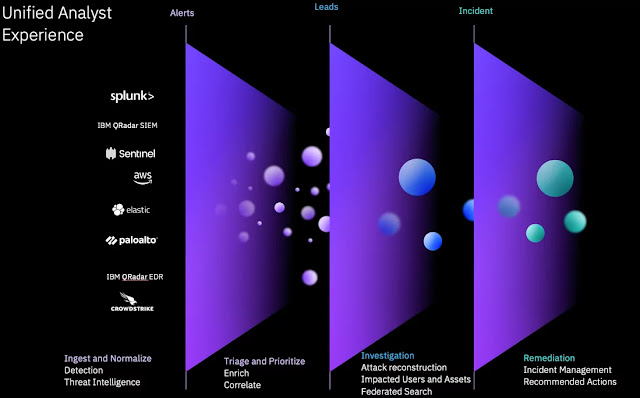
QRadar Log Insights provides a simplified and unified analyst experience (UAX) that enables your security operations team to search and perform analytics, automatically investigate incidents and take recommended actions using all security-related data, regardless the location or the type of the data source.
With QRadar Log Insights’ UAX, you get:
◉ AI-based risk prioritization: As data flows in, logs and alerts are automatically checked against security rules and indicators of compromise (IoC) from threat intelligence sources. After being enriched with business context, they’re processed by a self-learning engine that’s informed by past analyst actions. This engine identifies high fidelity findings and filters out false positives. AI-based risk scoring is then applied. Although the analyst didn’t have to do anything, all the steps and information about the events, threat intelligence and applied score is available for analysis.
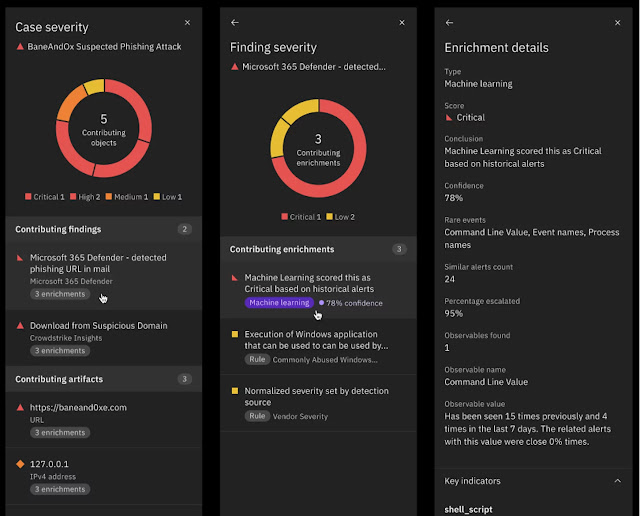
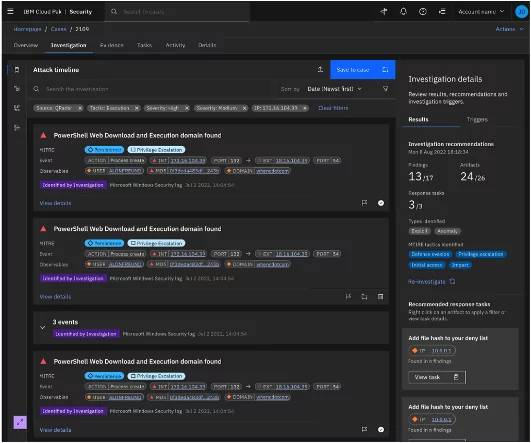
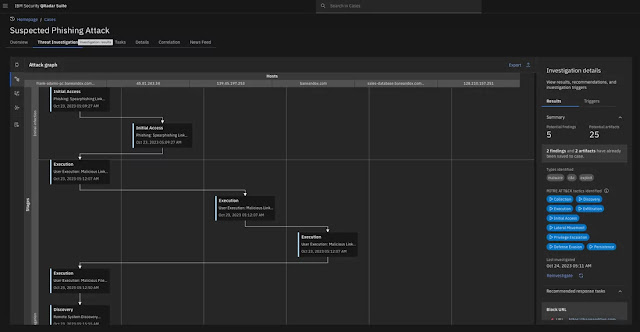
◉ Automated investigation: A case is automatically created for incidents above a risk threshold calculated using a combined score from correlated events. Events in a case are arranged on a timeline for a quick view of attack steps. All identified artifacts are collected as evidence, such as IoCs, IP and DNS addresses, host name, user IDs, vulnerability CVEs, etc. Additionally, findings continue to be correlated with artifacts collected on a sliding time window providing continuous monitoring into the future.
◉ Recommended actions: Based on the identified artifacts and techniques from the attack, Log Insights suggests pointed mitigation actions, ensuring a quick response and speedy containment.
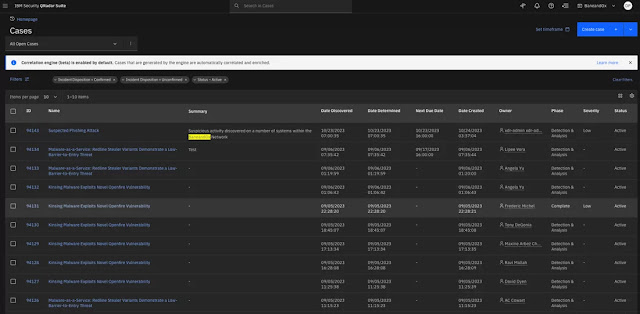
◉ Case management: Integrated case management streamlines collaboration and tracks progression toward resolution. Every piece of evidence is collected, appropriate action is recommended and those taken by peers are recorded.
◉ Insightful attack visualization: A comprehensive graphical visualization illustrates the attack path, highlighting the sequence and mapping attack stages to the impacted resources—known as the blast radius. This visualization empowers SOC analysts to gauge the impact, understand potential persistence techniques, and identify what areas are most important to address first.
Attack steps are also mapped to MITRE TTPs, offering detailed insights into adversarial actions and progress:
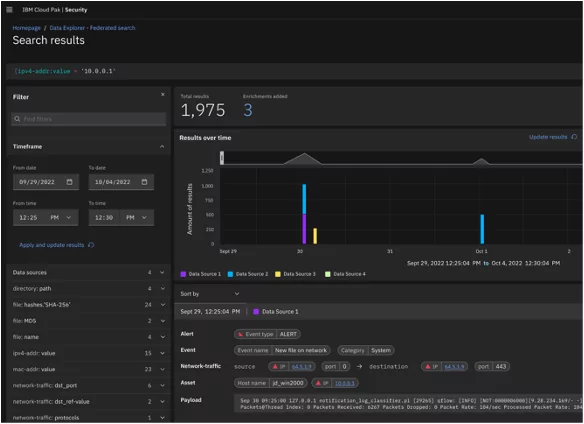
◉ Federated search: A high-performance search engine empowers threat hunting across all your data sources. From a single screen with a single query, search data from your security tools EDRs, SIEMs, NDRs, Log Mgt, Cloud, email security, etc. This capability enables extended investigations into third-party sources, on-prem and in other clouds, accommodating data not yet ingested into Log Insights. You can simultaneously query both the data within Log Insights and multiple external data sources, all included for no additional cost.
◉ Integrated threat intelligence: X-Force and community-sourced threat intelligence are continuously updated, autonomously tracking threat activities. This dynamic system keeps up with previously unseen threats enhancing detection capabilities.
UAX integrated suite of capabilities powered by AI and automation, streamlines risk prioritization, threat investigation and visualization, federated searching, and case management, enabling analysts to handle incidents with remarkable speed and efficiency.
Unlock analysts’ productivity with QRadar Log Insights
Disjointed information and fragmented workflows can significantly extend the amount of time security analysts spend on investigating and acting on security events. In cybersecurity, how your security team spends their time can mean the difference between simply analyzing a security event and dealing with a full-blown data breach incident. Every second counts.
To cope with the rising tide of data and alerts, organizations must transcend the limitations of manual processes. By integrating artificial intelligence and automation into their workflows, analysts are better equipped to keep pace with and respond to the rapidly intensifying landscape of cyber threats.
Unlock analyst’s productivity with a modern log management and security observability platform.








0 comments:
Post a Comment