Communication service providers (CSPs) are teaming up with hyperscalers to offer private wireless networks that are owned and fully managed by whoever builds them. A private wireless network (PWN) provides the same kind of connectivity as public wireless networks, and enterprises must weigh the pros and cons of private wireless networks using 5G technology. It is important to understand some of the common patterns, as well as the management aspects of such networks, including the components needed to create PWNs and their architecture.
Components of a private wireless network
There are many components that constitute a private wireless network, but these are the key required elements:
- Spectrum refers to the radio frequencies that are used for communications (and are allocated by the state). Choosing a licensed or unlicensed radio spectrum depends on coverage requirements, interference conditions and regulatory compliances.
- Network core is the control center that provides packet switching, policy control, authentication, session management, access and mobility function, routing and network management.
- Radio Access Network (RAN) includes Open RAN-based virtual centralized unit (vCU), virtual distribution unit (vDU), radio unit (RU), gateway and other equipment that enables wireless communication between end-user devices and the network core that is reliable, efficient and seamless.
When building out a private wireless network there is a need for supplementary elements such as orchestration, service assurance, management, monitoring and security. These components play a pivotal role in ensuring the seamless operation, optimization and security of the private wireless network, contributing to its resilience and high-performance capabilities.
There are essentially three types of companies that are involved in building these solutions:
- Telecommunications (telco) vendors like Nokia, Ericsson, Samsung and Mavenir
- Hyperscalers like IBM, AWS, Azure and GCP
- Communications service providers like AT&T, Verizon and TELUS
Telecommunication vendors partner with cloud providers to deliver private wireless networks for enterprises either directly or through communications service providers or systems integrator (SI) partners.
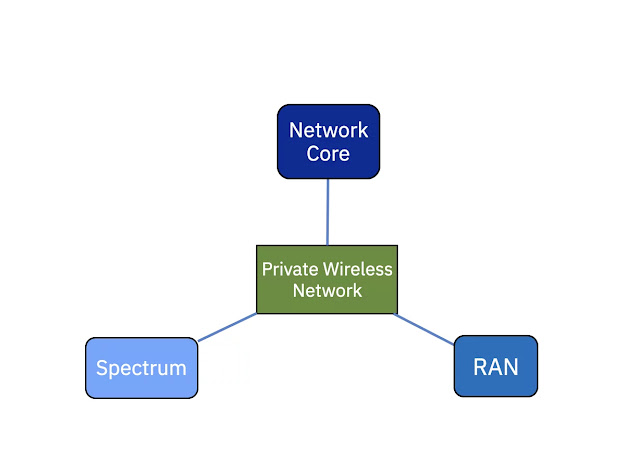
Figure 1. Network-related components of private wireless network
Figure 1 shows the networking components that a CSP would require so they can assist customers in configuring a private wireless network. These are standard network-related components that CSPs are used to deploying. Historically, many of these elements were constructed using dedicated hardware. However, a significant shift has occurred, with an increasing number of these components transitioning to a cloud-native, software-based paradigm: the virtualized (in most cases containerized) radio access network that includes related components like a vCU, a vDU and the virtualized network core.
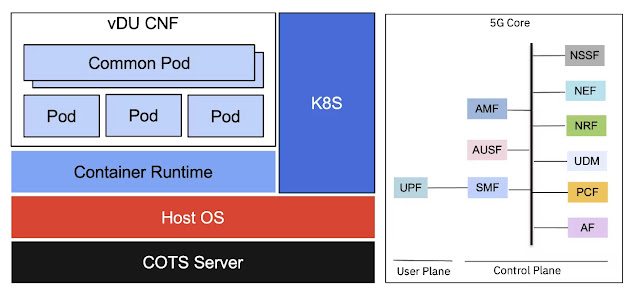
A representative container-based vDU architecture is shown as an example in Figure 2 to give the reader an idea of how software has replaced dedicated purpose-built hardware in network components. Figure 2 also shows the components in 5G core service-based architecture. All components are either virtualized or containerized. This is important because it has provided hyperscalers a huge opportunity in a space dominated by telcos.
Figure 2 vDU architecture and 5G core components
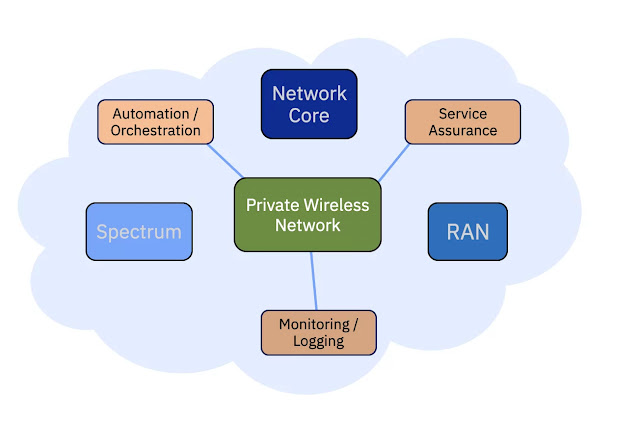
The other half of the solution is related to software components, which cloud providers bring to augment and complete the solution. They can range from automation scripts, to orchestration, to service assurance and even monitoring and logging. The most important aspect is that the hyperscaler provides the cloud platform to host the solution and the corresponding cloud services. These are shown in Figure 3 as beige-colored boxes.
Figure 3. Software-related support functions of private wireless network
Benefits of private wireless networks
These standalone networks can be deployed in industrial settings such as manufacturing shop floors, logistical warehouses, large hospitals, sports stadiums and enterprise campuses. Enterprises do not have to cater to the constraints of a public network. Instead, they can deploy and have control of a private network that meets their exact needs.
Figure 4 depicts an exemplar architecture where the private wireless network comprising the 5G RAN and 5G core, along with the edge applications, are deployed on a hyperscaler platform. One of the main requirements is that the PWN be deployed on-premises. That topology fits the IBM Cloud Satellite® paradigm wherein the on-premises location can be an IBM Cloud Satellite location that is connected to an IBM Cloud® region via a secure IBM Cloud Satellite link. This design could serve enterprise customers who are looking at proximity to required 5G network components, which offer low-latency and high-throughput capability.
Figure 4. Block diagram of a private wireless network
This architecture pattern fulfills the requirement of serving the end users, devices and applications closer to where they are. To support real-time, mission-critical use cases, user plane applications are placed in the IBM Cloud Satellite location. These satellite locations could be an on-prem edge datacenter or any public cloud location.
Architecting private wireless network in IBM Cloud
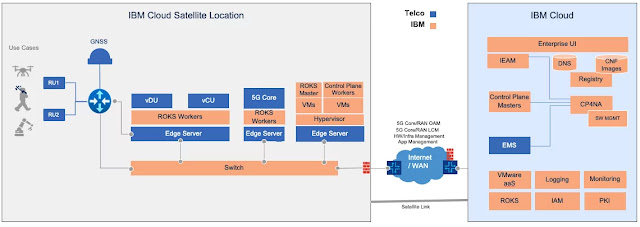
By implementing a private 5G network, large enterprises can bring a customized 5G network to their facility and keep it secure while using its high-speed, high-bandwidth and low-latency features. Like most networking solutions, there are two parts to this: the “managed from” components and the “managed to” components. The “managed from” components are hosted in the partnering hyperscalers cloud, and the “managed to” components are typically on the enterprise’s premises with secure high-speed connectivity between those two locations. In our example, IBM Cloud hosts the “managed from” components while the satellite location is running the “managed to” components.
Figure 5 shows a pattern where the private wireless network is deployed on-premises on the left (at a “remote” IBM Cloud Satellite location). The workloads running in that satellite location can access supporting services hosted in the IBM Cloud on the right. The network components provided by a telco are shown in blue. Most of those are deployed in the satellite location, but some telco management systems can run in the cloud and could potentially offer multitenancy capability to support multiple enterprises.
Figure 5. Private wireless network architecture in IBM Cloud Satellite on-premises location
Imagine a manufacturing plant that has different kinds of movable and stationary robots and other programmable devices operating within the plant. The company could choose to employ a private wireless network because that will speed up the inter-communications needed to operate the devices while keeping things secure.
In such a scenario, the manufacturing plant could be configured as a remote IBM Cloud Satellite location running the required workloads and cloud-related components on-premises. More importantly, the network connectivity required at the location would be provided by the PWN. This setup could be duplicated in the company’s other manufacturing units or their partner suppliers, across the state or country. Each unit would have its own PWN and be configured as an IBM Cloud Satellite location. All these satellite locations would be managed from an IBM Cloud region.
There is a master control plane running in IBM Cloud that monitors all the Satellite locations and provides centralized logging and security services as part of the managed services. IBM Cloud Site Reliability Engineers take care of all system upgrades and patching. We mentioned that the satellite link between the IBM Cloud Satellite location and IBM Cloud is a security-rich TLS 1.3 tunnel. Enterprises could also make use of IBM’s Direct Link service to connect. You will notice all the network connections described in this topology are secure.
IBM’s Cloud Pak for Network Automation (CP4NA), together with an Element Management System from a telco, would provide service orchestration and service assurance functions. IBM Cloud would provide monitoring and logging services along with identity access management for accessing the cloud environment. Additional network monitoring services could be provided by the CSP. This underscores the need for the cloud provider to work closely with the telco vendor. From an enterprise perspective, the enterprise user interface serves to mask the complexity, offering a unified interface for streamlined management, provisioning of services and comprehensive monitoring and logging. This user interface acts as a singular control hub, simplifying operations and enhancing overall efficiency.
Enterprises that want to set up a private wireless network can do so on their own or outsource it to a hyperscaler like IBM. Hyperscalers end up partnering with a CSP to build and manage these networks. It is very important to make sure that the network is built on a flexible platform and can be scaled in the future. Though enterprises should be cognizant of costs, more enterprises are choosing PWNs because they provide a secure and reliable alternative to a public network.
Source: ibm.com






0 comments:
Post a Comment